In December 2025, Self-Help Credit Union, a $2.4-billion institution based in Durham, North Carolina, filed a federal lawsuit against Fiserv, a major payments processor. The suit alleges Fiserv misrepresented its cybersecurity practices and then demanded excessive early termination fees when Self-Help attempted to leave. This case has become a focal point for compliance professionals, raising critical questions about vendor accountability, cybersecurity standards, and the enforceability of contractual terms in the financial services sector.
NETBankAudit experts have over 25 years of experience in vendor management, cybersecurity, and contract compliance audits for financial institutions. If you have any questions after reading this guide, please reach out to our team.
Overview of the Lawsuit: Vendor Accountability in Focus

Alleged Misrepresentation and Security Failures
Self-Help Credit Union’s complaint centers on Fiserv’s alleged misrepresentation of its cybersecurity practices and the imposition of excessive early termination fees. The credit union asserts that Fiserv failed to deliver on core security commitments, particularly regarding multi-factor authentication (MFA), and then sought to enforce contractual penalties despite these failures.
Industry Implications for Vendor Contracts
The lawsuit raises fundamental questions about the enforceability of aggressive vendor contracts when core performance and security standards are not met. It also highlights the growing expectation that vendors must be held accountable for both the quality of their services and their adherence to regulatory and industry standards.
Core Security Allegations: Multi-Factor Authentication and NIST Standards
Discrepancies in MFA Implementation
A central allegation is that Fiserv did not provide genuine multi-factor authentication for Self-Help’s systems, despite promising robust security controls. While Fiserv reportedly used advanced MFA—including token generators and biometric controls—for its own internal data, it offered clients much weaker protections. Specifically, Fiserv relied on email passcode challenges, sending one-time passwords to email addresses for authentication.
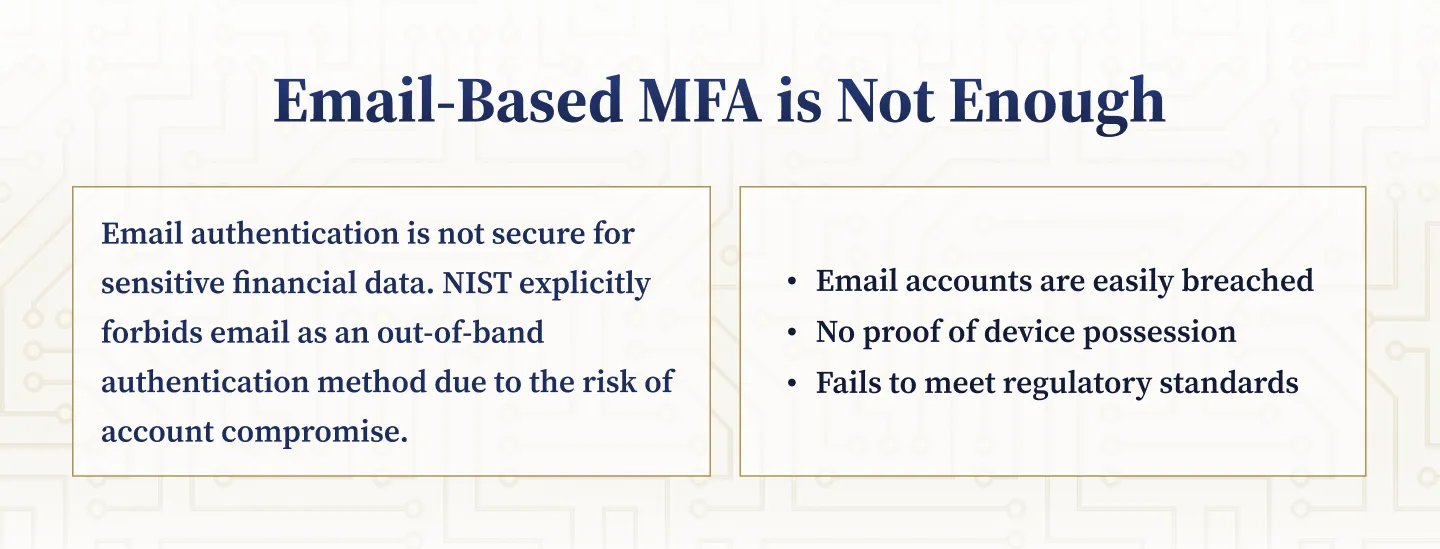
Why Email-Based MFA Is Inadequate
Email-based authentication is widely recognized as insufficient for high-security environments. The National Institute of Standards and Technology (NIST) explicitly prohibits the use of email for out-of-band authentication in its Special Publication 800-63B guidelines, citing the risk that email accounts can be compromised and do not prove possession of a separate device.
- NIST Guidance: NIST states that email “SHALL NOT be used for out-of-band authentication because it may be vulnerable to multiple threats.”
- Contractual Obligations: Self-Help’s Master Agreement required Fiserv to use the same care and discretion to protect client data as it does for its own information.
- Alleged Fraudulent Compliance: The complaint alleges Fiserv provided a compliance package that misrepresented its adherence to NIST standards and falsely claimed to utilize MFA.
Systems Without Any MFA
The lawsuit claims that at least one Fiserv system housing Self-Help member data required no MFA at all. This represents a significant security lapse and a direct violation of both contractual and regulatory expectations for protecting sensitive financial data.
The Early Termination Fee Dispute: Contractual Leverage or Ransom?
Fiserv’s Seven-Figure Fee Demand
When Self-Help Credit Union sought to migrate its data to a more secure provider, Fiserv allegedly demanded a seven-figure early termination fee. The credit union’s complaint likens this to a “ransom,” arguing that Fiserv’s ultimatum forced them to choose between paying the fee or leaving their data exposed on inadequately secured systems.
Legal and Ethical Questions Raised
This dispute brings to the forefront the issue of whether vendors can enforce punitive early termination fees when they have failed to meet core service and security obligations. The complaint, led by attorney Charles Nerko, asks: What should accountability look like when a core processor does not deliver on key commitments but still seeks to enforce significant penalties?
- Voidance of Fees: Self-Help is seeking to void the early termination fees entirely, requesting both monetary damages and a court order compelling Fiserv to secure the data.
- Broader Precedent: The outcome could set a precedent for how financial institutions challenge vendor contracts that include aggressive penalty clauses.
%201%20(1).svg)
%201.svg)
THE GOLD STANDARD INCybersecurity and Regulatory Compliance
Charles Nerko’s Track Record: A Pattern of Vendor Litigation
Multiple Credit Unions Take Action
Charles Nerko, Managing Partner of NERKO PLLC, has become a leading figure in representing credit unions against Fiserv. The Self-Help case is one of several similar lawsuits, each highlighting alleged security lapses and contractual overreach by Fiserv.
Previous Cases and Outcomes
Nerko previously represented Bessemer System Federal Credit Union in Pennsylvania, which alleged that Fiserv’s platform was “plagued with security vulnerabilities” and that Fiserv threatened legal action if the credit union discussed these issues with third parties. For more, see CyberScoop.
In June 2025, Cencap Federal Credit Union in Connecticut also filed suit, claiming Fiserv’s systems were vulnerable to “shockingly easy” cyberattacks due to inadequate login protections and lack of MFA. In at least one case, a credit union was allowed to exit its contract without paying early termination fees. For legal analysis, see Barclay Damon.
Fiserv’s Business and Legal Challenges: A Company in Crisis

Stock Collapse and Financial Underperformance
The Self-Help lawsuit comes at a time of significant turmoil for Fiserv. The company’s stock price has plummeted nearly 70% of its value since its March 2025 peak, with the most severe drop occurring after a disastrous third-quarter earnings report in October 2025. Fiserv missed analyst expectations by a wide margin, slashed its financial guidance, and saw its market capitalization drop by nearly $30 billion in a single day.
Factors Behind the Decline
Several factors contributed to Fiserv’s collapse, including overreliance on growth in Argentina, slower-than-expected performance in its Clover point-of-sale platform, and a decline in Financial Solutions revenue.
CEO Mike Lyons, who assumed the position in May 2025, acknowledged the company’s underperformance, stating: "Our current performance is not where we want it to be nor where our stakeholders expect it to be."
Shareholder Lawsuits and Allegations of Misleading Investors
Multiple shareholder class action lawsuits have been filed against Fiserv and its executives since June 2025, alleging the company misled investors about its growth prospects and the basis for its 2025 financial guidance. These lawsuits allege that Fiserv's July "re-underwriting" of its initiatives and products, which had assured investors that delayed projects were fundamentally sound, was misleading, as the company later admitted that its July guidance would have been "objectively difficult to achieve even with the right investment and strong execution."
Additionally, a separate securities class action alleges that Fiserv artificially inflated Clover's performance by secretly migrating merchants from its legacy Payeezy platform, temporarily boosting revenue metrics while concealing underlying business challenges.
Leadership and Restructuring Response
Executive Changes and Strategic Shifts
In response to the financial crisis, Fiserv announced significant leadership changes and a restructuring plan called "One Fiserv." Mike Lyons brought in Takis Georgakopoulos (current COO) and Dhivya Suryadevara (formerly CEO of Optum Financial at UnitedHealth) as Co-Presidents, and Paul Todd (former CFO of Global Payments) as the new CFO, effective in late 2025. The company also announced plans to transfer its stock listing from the New York Stock Exchange to Nasdaq.
Broader Industry Context: Vendor Accountability and Contract Negotiation
Industry-Wide Implications for Vendor Management
The Self-Help case is not an isolated incident. It is part of a broader pattern of financial institutions challenging the security practices and contractual terms of large core processors. At stake is the question of whether vendors can lock clients into unfavorable contracts indefinitely, regardless of service quality or security performance. The complaint explicitly frames the issue as one of leverage and coercion, arguing that vendors should “earn long-term relationships with credit unions through reliable performance and appropriate safeguards, not penalty-driven leverage.”
Key Takeaways for Compliance Professionals
For compliance officers and vendor managers, the case underscores the importance of negotiating clear contract terms, understanding security requirements, and being prepared to challenge inadequate early termination fees through litigation if necessary.
- Contract Clarity: Ensure that vendor contracts specify security standards and performance metrics, with clear remedies for non-compliance.
- Due Diligence: Regularly review vendor security practices and compliance documentation, and verify claims against industry standards such as NIST.
- Exit Strategies: Negotiate reasonable termination clauses and be prepared to challenge excessive fees if the vendor fails to meet obligations.
Lessons Learned: Strengthening Vendor Oversight and Cybersecurity
Best Practices for Financial Institutions
The Self-Help lawsuit offers several important lessons for financial institutions seeking to strengthen their vendor oversight and cybersecurity posture. By proactively addressing these areas, institutions can reduce risk and improve their ability to hold vendors accountable.
Vendor Selection and Onboarding
Carefully vet vendors for their security practices, regulatory compliance, and track record. Require detailed documentation of security controls and insist on independent audits or certifications where possible.
Ongoing Monitoring and Compliance
Establish regular review processes for vendor performance and security compliance. Use third-party assessments and penetration testing to validate vendor claims and identify potential vulnerabilities.
Contractual Safeguards
Negotiate contracts that include specific security requirements, clear definitions of material breach, and reasonable exit provisions. Avoid clauses that allow vendors to impose excessive penalties for early termination, especially when tied to failures in core service delivery.
Incident Response and Escalation
Develop clear protocols for escalating concerns about vendor performance or security lapses. Ensure that contracts provide for timely remediation and, if necessary, legal recourse.
How NETBankAudit Can Help: Vendor Management and Cybersecurity Assurance
Vendor Management Assessment
NETBankAudit provides dedicated Vendor Management assessments that evaluate your entire outsourcing risk management process. We review how you assess vendor risk, document due diligence, select technology service providers, and monitor them over time, with specific attention to FFIEC expectations for vendor risk assessment, due diligence, and ongoing monitoring.
As part of this work, we audit vendor contracts themselves. Our reviewers examine security requirements, data protection provisions, performance and service level terms, breach notification obligations, and exit and termination language, including early termination fees. The goal is to identify where contract terms do not align with your risk appetite, regulatory expectations, or the services actually delivered.
Value-Add Consulting Support
NETBankAudit also provides consulting support for institutions that need a more hands-on approach. We regularly assist community banks and credit unions with contract reviews before renewals or core conversions, help management teams understand where leverage exists in negotiations, and offer practical recommendations to rebalance risk and improve vendor accountability.
If your institution is concerned about vendor security, contract compliance, or the risks of early termination fees, contact NETBankAudit today. Our experts are ready to help you navigate these challenges and protect your organization’s interests.
.avif)

.svg)

.webp)

.webp)




.webp)
.png)




.webp)

.webp)











.webp)



.webp)

%201.webp)
.webp)
%20(3).webp)


.webp)


%20Works.webp)


.webp)




.webp)
%20(1).webp)

.webp)










.webp)
.webp)

.webp)
.webp)
.webp)
.webp)
.webp)
.webp)
%201.svg)