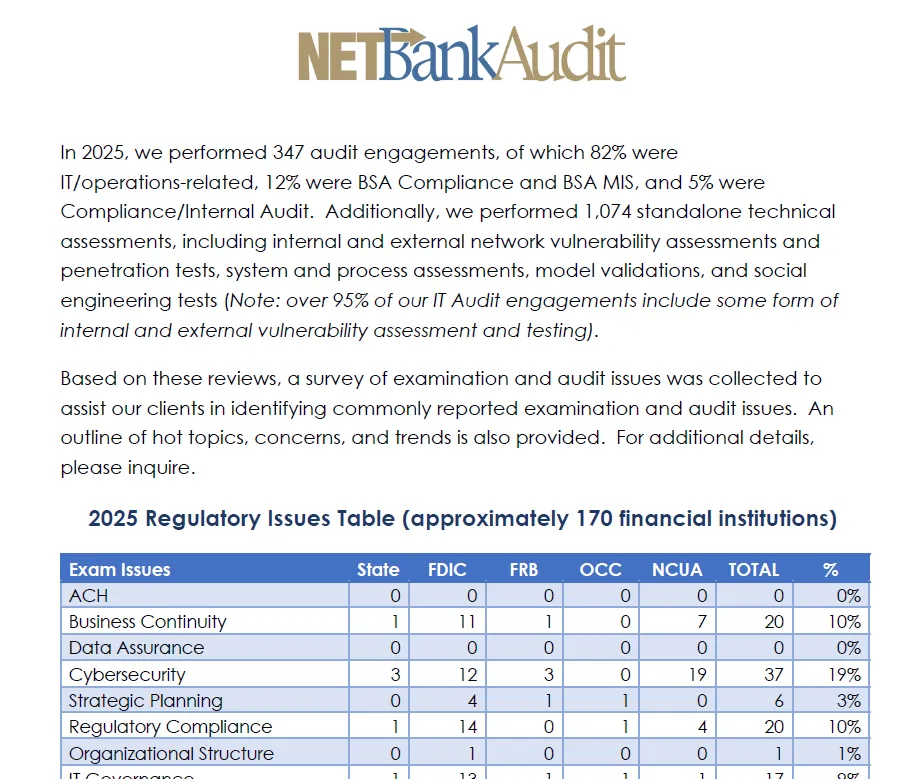
Introduction to Social Engineering in Cybersecurity
Social engineering testing is a critical component of cybersecurity for financial institutions, focusing on the human element that technology alone cannot fully protect. Social engineering attacks exploit psychological manipulation—rather than technical vulnerabilities—to deceive employees and gain unauthorized access to sensitive information or systems. Despite robust investments in firewalls, encryption, and monitoring, attackers circumvent even advanced defenses by preying on human behavior, which is inherently inconsistent and difficult to control.
The threat is not hypothetical: According to industry research, 84% of organizations have experienced at least one social engineering attack in the past year2. The FBI’s Internet Crime Complaint Center (IC3) reports that business email compromise (BEC) and CEO fraud schemes have resulted in over $2.3 billion in losses2. These attacks persist because they exploit trust, authority, urgency, and curiosity—psychological triggers that are difficult to eliminate through technology alone.
- Definition: Social engineering is the art of manipulating people to give up confidential information or perform actions that compromise security1.
- Scope: Attacks target employees at all levels, from frontline staff to executives.
- Impact: Financial losses, regulatory penalties, and reputational harm can be severe.
Reinforce Your First Line of Defense with NETBankAudit
NETBankAudit helps financial institutions defend against social engineering threats through tailored testing that includes phishing emails, vishing calls, and physical intrusion attempts. These ethical simulations assess employee responses without assigning blame, focusing instead on improving institutional readiness. Coupled with a thorough review of training programs and policies, NETBankAudit delivers detailed reporting and actionable recommendations to strengthen internal defenses and foster a security-first culture.
Types of Social Engineering Attacks: Tactics That Target Financial Institutions
Social engineering attacks come in many forms, each exploiting different aspects of human psychology and organizational processes. Financial institutions, with their complex structures and valuable assets, are frequent targets for a wide range of social engineering tactics. Understanding these attack types is essential for designing effective social engineering testing programs and building robust defenses.
Phishing: The Most Prevalent Social Engineering Threat
Phishing remains the most common and damaging form of social engineering attack. In a typical phishing campaign, attackers send emails that appear to come from legitimate sources, such as bank executives, IT departments, or trusted vendors. These emails often contain urgent requests to click on a link, download an attachment, or provide sensitive information. The links may lead to fake websites designed to harvest login credentials, while attachments may contain malware that compromises the recipient’s device.
- Emails mimic trusted brands or internal contacts
- Links redirect to credential-harvesting sites
- Attachments may install ransomware or spyware
- Often timed to coincide with busy periods or organizational changes

Vishing: Voice-Based Deception
Vishing, or voice phishing, involves fraudulent phone calls designed to trick employees into revealing confidential information or performing unauthorized actions. Attackers may use caller ID spoofing to impersonate bank officials, IT support staff, or even law enforcement. These calls often create a sense of urgency, such as claiming there is a security breach that requires immediate action.
A notable example involved attackers posing as IT support and convincing employees to reset passwords or provide remote access to critical systems. Social engineering testing for vishing typically involves simulated calls to evaluate how employees handle unexpected or suspicious requests over the phone.
Smishing: Exploiting Trust in SMS Communication
Smishing, or SMS phishing, leverages text messages to deceive recipients into clicking malicious links or divulging sensitive information. These messages may appear to come from trusted sources, such as a bank’s fraud department, and often contain urgent warnings about account activity or requests to verify personal details.
- Texts claim accounts are locked or compromised
- Links lead to fake login pages or malware downloads
- Requests for immediate action to “restore access”
Pretexting: Building Trust Through Fabricated Scenarios
Pretexting is a sophisticated form of social engineering in which attackers create elaborate stories or impersonate trusted figures to extract sensitive information. For example, an attacker might pose as an external auditor or IT consultant, requesting access to systems or confidential data under the guise of a legitimate business need.
This method often involves extensive research and social engineering testing to identify potential targets and craft believable scenarios. Pretexting can be particularly effective in hierarchical organizations where employees are accustomed to following instructions from authority figures.
Baiting: Luring Victims with Promises of Value
Baiting attacks entice victims with the promise of something valuable, such as free software, exclusive content, or even physical items like USB drives. When the victim takes the bait—by downloading a file or plugging in a device—they inadvertently install malware or grant the attacker access to internal systems.
- Free “gifts” left in public areas (USB drives, CDs)
- Online offers for free software or media downloads
- Malware payloads hidden in seemingly legitimate files
Reverse Social Engineering: When Victims Seek Out the Attacker
Reverse social engineering flips the traditional attack model by positioning the attacker as a helpful expert or support resource. The attacker creates a problem—such as a fake system error or security alert—and then offers assistance, prompting the victim to reach out for help. This approach increases the likelihood of trust and compliance, as the victim initiates the interaction.
Tailgating and Piggybacking: Physical Security Breaches
Not all social engineering attacks are digital. Tailgating and piggybacking involve gaining physical access to restricted areas by following authorized personnel through secure doors. Attackers may pose as delivery personnel, maintenance workers, or even fellow employees to bypass access controls.
- Following staff through secure entrances
- Impersonating delivery or maintenance personnel
- Accessing sensitive areas without proper credentials
Robocalls: Automated Attacks at Scale
Robocalls are automated phone calls used to deliver fraudulent messages to large numbers of employees or customers. These calls may claim to be from the bank’s fraud department, urging recipients to provide account information or reset passwords. The scale and automation of robocalls make them a persistent threat, especially for large financial institutions.
Notable Real-World Examples
- Equifax Data Breach: Phishing emails led to the compromise of 145.5 million user records, resulting in massive financial and reputational damage.
- CEO Fraud: Attackers impersonated executives to authorize fraudulent wire transfers, costing organizations billions.
- Banking Sector Attacks: Multiple banks have reported losses due to vishing and pretexting schemes targeting employees with access to sensitive systems.
The Social Engineering Attack Lifecycle
Understanding the typical lifecycle of a social engineering attack helps institutions anticipate and disrupt these threats. The stages include:
- Reconnaissance: Attackers gather information about the target organization and its employees using public sources, social media, or data breaches.
- Engagement: The attacker initiates contact, often through email, phone, or social media, establishing trust or authority.
- Exploitation: The attacker manipulates the victim into revealing sensitive information, clicking a malicious link, or granting access.
- Execution: The attacker uses the obtained information or access to compromise systems, steal funds, or escalate privileges.
- Covering Tracks: The attacker may delete logs, use anonymizing tools, or otherwise attempt to avoid detection and attribution.
Emerging Social Engineering Threats (2024–2025)
Social engineering tactics continue to evolve, with attackers leveraging new technologies and trends:
- AI-Generated Voice Scams: Attackers use artificial intelligence to mimic the voices of executives or colleagues, making vishing attacks more convincing.
- Deepfake Video Impersonation: Video calls or messages are manipulated to appear as if they come from trusted individuals, increasing the risk of high-value fraud.
- QR Code Phishing (Quishing): Malicious QR codes are distributed via email, posters, or websites, directing victims to phishing sites or malware downloads.
Staying ahead of these threats requires continuous monitoring, updated training, and adaptive testing strategies.
%201%20(1).svg)
%201.svg)
THE GOLD STANDARD INCybersecurity and Regulatory Compliance

Research and Statistics: The Scale and Impact of Social Engineering Attacks
Recent studies highlight the growing prevalence and financial impact of social engineering attacks on financial institutions. Nearly half of large organizations report experiencing more than 25 social engineering incidents over a two-year period, with the average cost per incident exceeding $100,0001. The FBI has documented over $2.3 billion in losses from CEO fraud and business email compromise schemes2. Notably, employees are the entry point for 91% of successful cyberattacks6, underscoring the importance of human-focused defenses.
The Equifax breach, caused by a successful phishing attack, exposed the personal data of 145.5 million individuals and resulted in over $700 million in settlements and regulatory fines.
Training and Awareness Programs for Financial Institutions
Effective social engineering testing is only part of the solution. Comprehensive training and awareness programs are essential for empowering employees to recognize and resist manipulation attempts. Training should be interactive, ongoing, and tailored to the specific risks faced by different departments and job functions.
- Interactive, scenario-based learning that reflects real-world threats
- Role-specific modules tailored to different job functions and risk profiles
- Regular updates based on emerging threats and lessons learned from social engineering testing
- Clear reporting procedures and escalation paths for suspected incidents
- Recognition and rewards for employees who demonstrate strong security awareness
Simulated social engineering scenarios—such as phishing emails, vishing calls, and smishing messages—help assess readiness and reinforce best practices. Regular updates and open communication foster a culture where employees feel comfortable reporting suspicious activity.
Conducting Internal Social Engineering Tests
Internal social engineering testing is a proactive approach to uncovering weaknesses before attackers can exploit them. By simulating real-world attack scenarios, organizations can evaluate the effectiveness of their training programs, identify gaps in policies and procedures, and strengthen their overall security posture.
- Email phishing campaigns to test recognition of suspicious messages
- Vishing calls to assess response to fraudulent phone requests
- Smishing attempts to evaluate mobile device security awareness
- Physical security tests, such as tailgating simulations
The process begins with clear objectives and success criteria, followed by documentation and analysis of outcomes. Regular internal testing fosters a culture of continuous improvement and helps employees become more adept at recognizing and responding to threats.
Third-Party Social Engineering Assessments
While internal testing is valuable, third-party assessments provide an objective, comprehensive evaluation of an organization’s security posture. External assessors bring fresh perspectives, specialized knowledge, and access to the latest threat intelligence, enabling a more thorough review.
- Unbiased evaluation of security controls and employee awareness
- Access to specialized expertise and up-to-date threat intelligence
- Identification of blind spots and emerging risks
- Actionable recommendations for enhancing defenses
- Improved regulatory compliance and audit readiness
Internal vs. Third-Party Social Engineering Testing: Comparison Table
Regulatory Guidance and Frameworks
Financial institutions must align their social engineering testing and awareness programs with regulatory frameworks and industry standards. Key references include:
- FFIEC Cybersecurity Assessment Tool: Provides guidance for banks and credit unions on social engineering risk management.
- GLBA (Gramm-Leach-Bliley Act): Requires financial institutions to protect customer information, including through employee training and testing.
- NIST SP 800-53: Security controls such as SI-4 (Information System Monitoring), AT-2 (Security Awareness Training), and CA-8 (Penetration Testing) address social engineering risks.
- OCC and FDIC Guidance: Emphasize the importance of employee awareness, incident response, and regular testing in their cybersecurity handbooks.
Adhering to these frameworks not only reduces risk but also demonstrates due diligence to regulators and stakeholders.
Consequences of Social Engineering Attacks
The consequences of successful social engineering attacks can be severe and far-reaching for financial institutions. These include:
- Direct financial losses from fraudulent transactions, data theft, and ransom payments
- Regulatory penalties, increased audits, and compliance enforcement
- Reputational harm and loss of customer trust
- Operational disruptions and increased recovery costs
- Internal policy revisions and heightened scrutiny of employee actions
For example, the Equifax breach resulted in over $700 million in settlements and ongoing regulatory scrutiny. In addition, the FDIC and OCC have issued enforcement actions and fines against banks that failed to implement adequate social engineering controls.
Validate Your Social Engineering Resilience with NETBankAudit
Social engineering attacks continue to be one of the most effective ways malicious actors infiltrate financial institutions, not through firewalls, but through people. NETBankAudit’s Social Engineering Testing program is designed to identify these human-layer vulnerabilities through real-world simulation and comprehensive evaluation.
Our services include email phishing, vishing (phone-based social engineering), and physical testing, all tailored to your institution’s unique environment. These simulations mimic real attack scenarios, such as suspicious emails with embedded links, impersonation calls requesting sensitive information, or onsite visits attempting unauthorized access. Every test is conducted ethically and discreetly, with a focus on policy adherence rather than individual performance.
Alongside these tests, NETBankAudit conducts a Security Awareness Assessment to review your institution’s information security policies, training programs, and internal communication protocols. We interview key personnel, evaluate training frequency and content, and assess whether employees are effectively prepared to recognize and respond to social engineering threats.
Following the engagement, you receive a detailed report documenting each test, including employee responses, breakdowns of successful and unsuccessful attempts, and clear, actionable recommendations to improve training, tighten policies, and reinforce a culture of awareness.
Partner with NETBankAudit to identify weaknesses before attackers do. Contact us today to schedule a customized social engineering assessment.
Sources:
1. Wang, Z., Sun, L., & Zhu, H. (2020). Defining Social Engineering in Cybersecurity. IEEE Access.
2. Aldawood, H., Alashoor, T., & Skinner, G. (2020). Does Awareness of Social Engineering Make Employees More Secure? International Journal of Computer Applications, 177(38).
3. Spinapolice, M. (2011). Mitigating the Risk of Social Engineering Attacks. Rochester Institute of Technology.
4. Wang, Z., Zhu, H., Liu, P., & Sun, L. (2021). Social Engineering in Cybersecurity: A Domain Ontology and Knowledge Graph Application Examples. Cybersecurity.
5. Salahdine, F., & Kaabouch, N. (2019). Social Engineering Attacks: A Survey. Future Internet, 11(4), 89.
6. Cybersecurity and Infrastructure Security Agency (CISA). (2021). Avoiding Social Engineering and Phishing Attacks. Retrieved from https://www.cisa.gov.
7. Syafitri, W., Shukur, Z., Mokhtar, U. A., Sulaiman, R., & Ibrahim, M. A. (2022). Social Engineering Attacks Prevention: A Systematic Literature Review. IEEE Access.
.avif)

.svg)

.webp)


.webp)




.webp)
.png)




.webp)

.webp)










.webp)



.webp)

%201.webp)
.webp)
%20(3).webp)


.webp)


%20Works.webp)


.webp)




.webp)
%20(1).webp)

.webp)










.webp)
.webp)

.webp)
.webp)
.webp)
.webp)
.webp)
.webp)
%201.svg)