The financial services industry is experiencing a rapid shift to cloud computing, with community banks, regional banks, credit unions, and other regulated institutions embracing cloud platforms for agility, scalability, and cost savings. However, this transition has also created a significant cloud security gap, exposing organizations to new regulatory, technical, and operational risks.
As the attack surface expands, thousands of unsecured pathways can leave sensitive systems and data vulnerable to cyber threats. Understanding and addressing these risks is now a top priority for compliance, risk, information security, technology, audit, and executive leadership teams.
NETBankAudit experts have over 25 years of experience in cloud security audits and compliance for financial institutions. If you have any questions after reading this guide, please reach out to our team.
What Is the Cloud Security Gap in Financial Services?
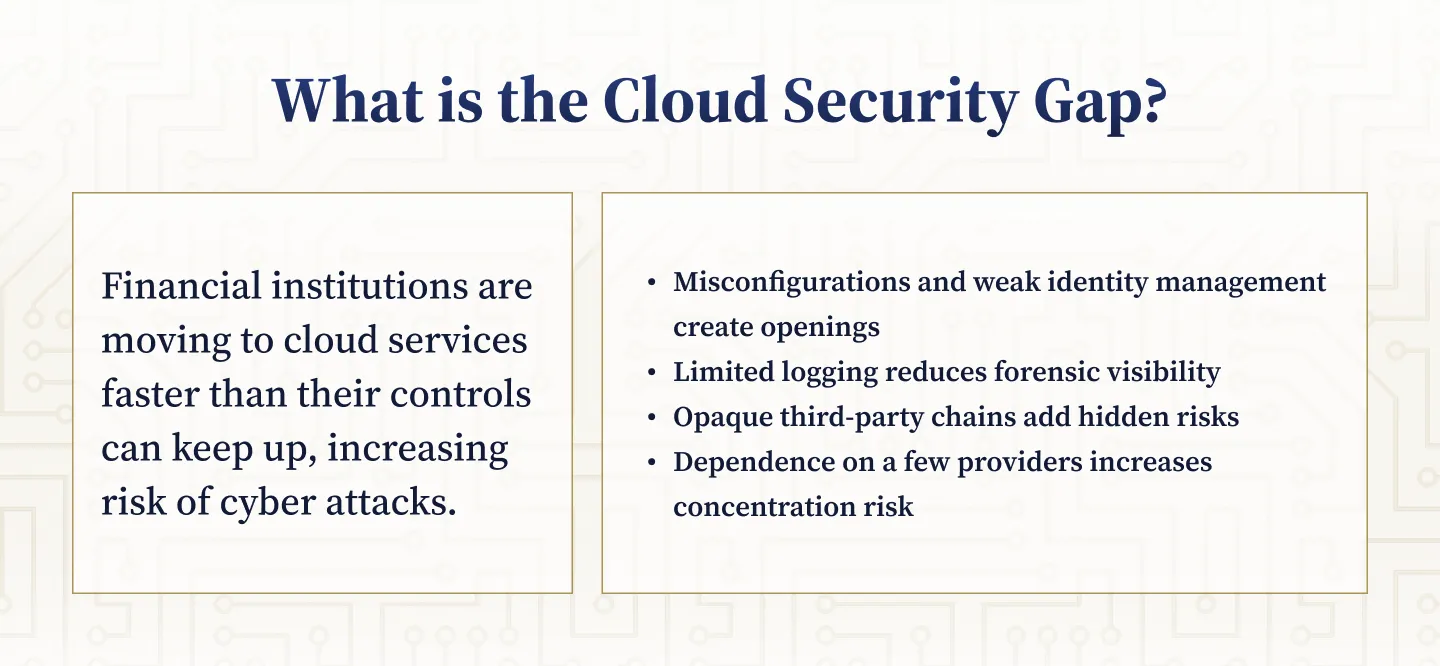
Defining the Cloud Security Gap for Banks and Credit Unions
The cloud security gap refers to the exposures that arise when financial institutions migrate to cloud services faster than they can adapt their governance, controls, and operational practices. This gap is not just a technical issue; it is a combination of misconfigurations, weak identity and key management, insufficient logging, opaque third-party chains, and concentration risk. Regulatory bodies such as the FFIEC, NIST, CISA, and the U.S. Treasury have all identified these issues as material risks for the sector.
Key Drivers of Cloud Security Gaps in Financial Institutions
Several factors contribute to the cloud security gap in the financial services industry. These include:
- Rapid cloud adoption without corresponding updates to risk management frameworks
- Complex multi-cloud environments with inconsistent controls
- Identity sprawl and weak authentication practices
- Insufficient logging and limited forensic capabilities
- Opaque third-party and sub-outsourcing relationships
- Concentration risk due to reliance on a small number of cloud providers
Regulatory Requirements for Cloud Security in Financial Services
FFIEC, NIST, and CISA Guidance on Cloud Security Controls
U.S. regulators have issued clear expectations for cloud security in financial institutions. The FFIEC Joint Statement on Security in a Cloud Computing Environment highlights the need for strong governance, risk identification, data classification, identity and access management, encryption, logging, incident response, and vendor controls. The Interagency Guidance on Third-Party Relationships further outlines requirements for due diligence, contract structuring, oversight, and exit strategies, all of which are critical for cloud provider relationships.
Essential U.S. Regulatory Documents for Cloud Security
- FFIEC IT Examination Handbook: Covers cloud architecture, configuration management, resilience, and monitoring.
- NYDFS Cybersecurity Regulation 23 NYCRR 500: Mandates risk assessments, encryption, MFA, asset management, privileged access management, logging, and third-party security policies for cloud and SaaS.
- SEC Cybersecurity Disclosure Rules: Require disclosure of material cyber risks and incidents, including those involving cloud services and third-party compromises.
- CISA Cloud Security Technical Reference Architecture: Provides secure cloud patterns, logging strategies, and telemetry for detection and response.
- FedRAMP Baselines: Serve as a benchmark for cloud service provider security control posture and continuous monitoring.
Top Cloud Security Risks Facing Financial Services Organizations
Identity and Access Management Weaknesses in Cloud Environments
The expansion of identities; users, service principals, machine identities, API keys, and tokens across multiple cloud and SaaS platforms creates numerous access pathways. Inadequate MFA, excessive privileges, and legacy protocols are frequent root causes of cloud intrusions. Federated SSO misconfigurations and token theft are also exploited to pivot across environments.
- Implement phishing-resistant MFA (such as FIDO/WebAuthn) for admins and high-risk users
- Enforce least privilege with just-in-time elevation and robust conditional access
- Harden IdP integrations and session controls
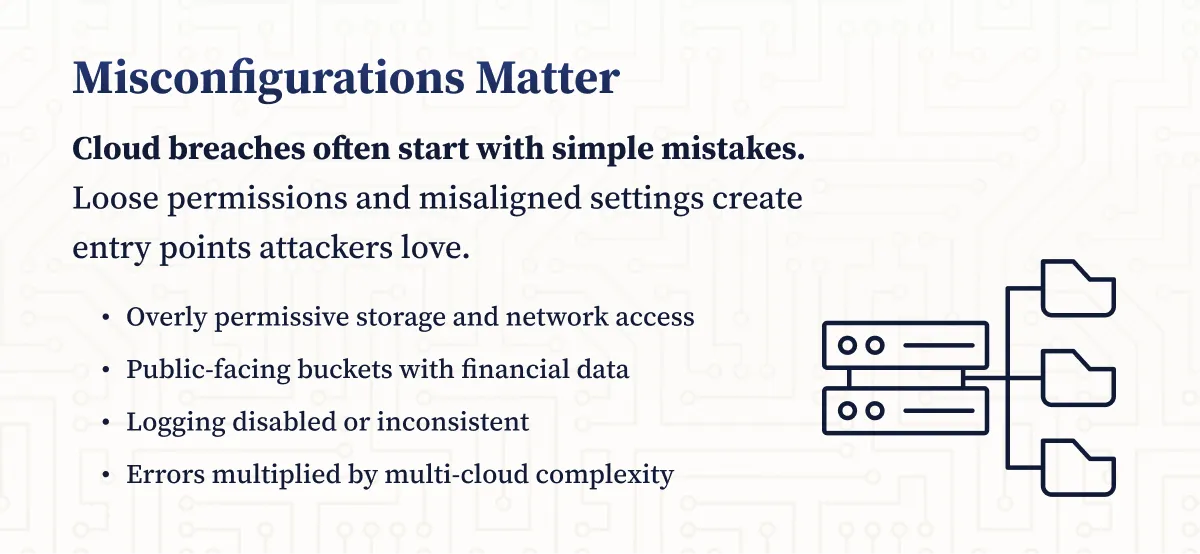
Cloud Misconfiguration and Insecure Defaults in Financial Institutions
Cloud misconfiguration is a leading cause of breaches in the financial sector. Overly permissive storage or network access, public exposure of data stores, weak security group rules, and disabled logging are common issues. Infrastructure-as-code drift and multi-cloud inconsistency further increase error rates.
- Adopt policy-as-code and configuration baselines
- Continuously monitor for drift and enforce secure defaults
- Leverage domain-specific guidance for containers and microservices
Logging, Telemetry, and Forensics Gaps in Cloud Security
Inconsistent and sometimes costly access to logs, lack of standardized telemetry, and limited incident forensic support impede detection and regulatory reporting. Regulators expect institutions to ensure logs are generated, retained, protected, and reviewable to meet incident response and examination needs.
- Centralize cloud control-plane, data-plane, and IdP logs
- Protect log integrity and retain logs per regulatory and forensic requirements
- Integrate cloud telemetry with SIEM/SOAR platforms
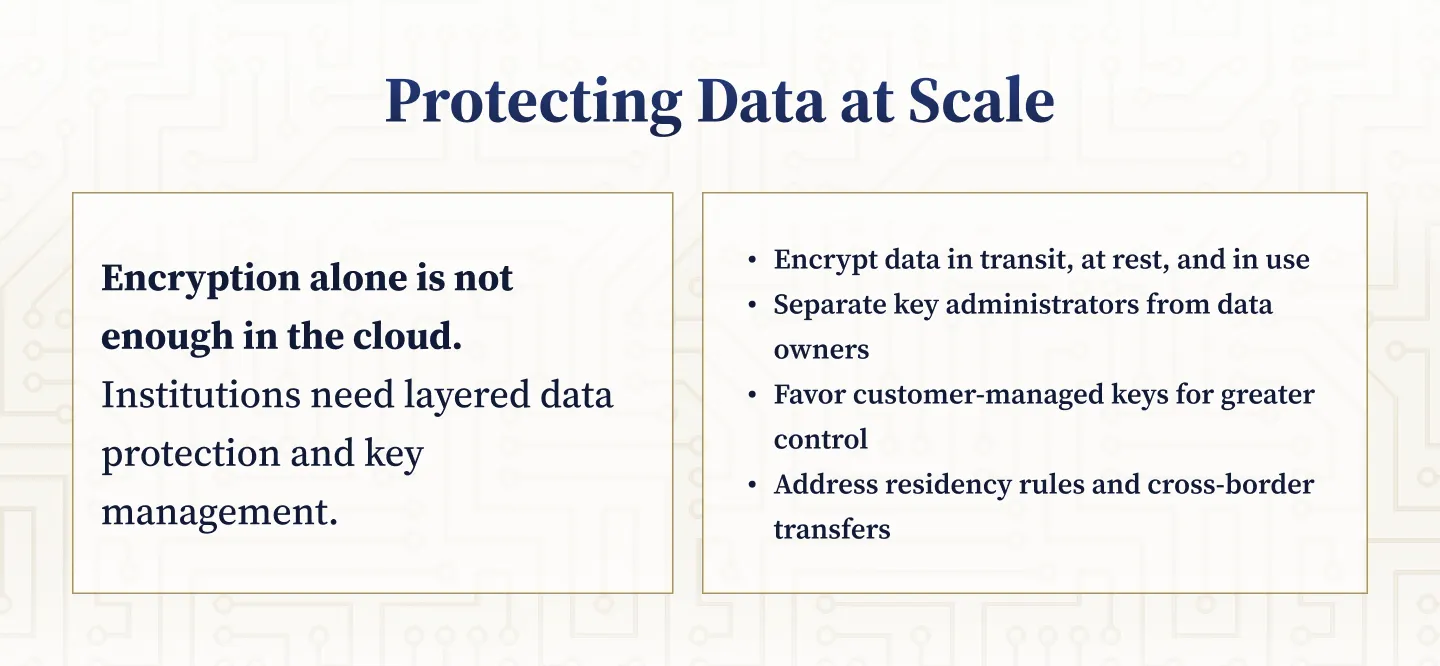
Data Protection and Key Management Challenges in the Cloud
Data must be classified and protected in transit, at rest, and in use with strong cryptography. Poorly segregated keys, inadequate customer-managed keys, or lack of crypto-shredding options are material risks. Data residency, cross-border transfer, and lawful access issues require both contractual and technical controls.
Third-Party and Sub-Outsourcing Risks in Cloud Services
Cloud supply chains involve multiple sub-processors, making it critical to map sub-outsourcing, ensure audit/access rights, and maintain transparency. Visibility gaps increase operational and compliance risk for financial institutions.
Concentration Risk and Operational Resilience in Cloud Adoption
Dependence on a small number of cloud providers creates sector-level concentration risk. Without diversification and exit playbooks, prolonged outages or vendor failure can become systemic risks for the financial sector.
Incident Response and Reporting in Cloud Environments
Shared responsibility models often break down during incidents when roles and logging are not pre-negotiated. Regulators expect timely detection, clear escalation, effective coordination with providers, and compliance with incident reporting timelines.
Application, API, and DevOps Risks in Financial Cloud Deployments
Rapid CI/CD and microservices increase exposure to dependency vulnerabilities, secrets leakage, and software supply chain attacks. API abuse and weak authorization are common attack vectors in cloud environments.
%201%20(1).svg)
%201.svg)
THE GOLD STANDARD INCybersecurity and Regulatory Compliance
Cloud Security Control Objectives for Financial Institutions

Governance and Risk Management for Cloud Security
Board and management oversight of cloud strategy and risk appetite is essential. Cloud risk assessment must be integrated with enterprise risk, including concentration and systemic risk. The shared responsibility model should be documented per service, with named control owners and testing coverage.
Identity and Access Management Best Practices for Cloud Security
Phishing-resistant MFA for admins and high-risk users is required. Least privilege with role-based access, just-in-time elevation, and session recording for break-glass scenarios are recommended. Service principal and API key governance, including rotation, scoping, and inventory, should be enforced.
Configuration, Network, and Workload Security in the Cloud
Baseline configurations and policy-as-code, continuous compliance monitoring, segmentation, private endpoints, and deny-by-default network policies are all critical. Container and serverless hardening, image provenance, and runtime controls should be implemented.
Data Protection and Cryptography for Cloud Environments
Data classification and tagging, encryption at rest and in transit using FIPS-validated modules, and key management with separation of duties are required. Data residency and lawful access must be addressed both contractually and technically.
Logging, Monitoring, and Detection for Cloud Security
Centralize and protect logs, retain them per regulatory and forensic needs, and detect/respond to anomalous activity. Integrate cloud telemetry with SIEM/SOAR platforms.
Incident Response and Business Continuity Planning for Cloud
Develop business continuity playbooks with CSP roles, contact paths, and data acquisition steps. Test incident response jointly with CSPs and meet regulatory reporting timelines.
Third-Party Risk Management and Cloud Contracts
Conduct due diligence on security certifications, resilience evidence, incident response support, and sub-processor mapping. Strengthen contracts with audit/access rights, log/forensic access, breach notification SLAs, sub-outsourcing transparency, and exit assistance.
Operational Resilience and Concentration Risk Mitigation
Map dependencies to critical services, define impact tolerances, and develop exit strategies. Test data portability, environment rebuild runbooks, and alternate provider feasibility.
Actionable Cloud Security Program for Community and Regional Banks
The best way to stay protected is to bring in experts who live and breathe this work every day. NETBankAudit specializes in helping community and regional banks build and maintain effective cloud security programs. We translate regulatory expectations into actionable controls and provide assurance that risks are being managed properly. Below are some steps to take to enhance your security posture.
Immediate Steps: 0–90 Days to Reduce Cloud Security Risk
Immediate actions can significantly reduce risk. Focus on identity, configuration, and logging controls:
- Adopt phishing-resistant MFA for admins and remote/cloud access; disable legacy authentication
- Inventory all cloud and SaaS tenants; enumerate privileged roles and service principals; revoke unused accounts/keys
- Turn on and forward core logs; set retention aligned to incident response and legal holds
- Block public access to storage; require private endpoints; enforce TLS 1.2+ everywhere
- Encrypt sensitive datasets with customer-managed keys; restrict key administrators separate from data owners
- Confirm incident response contacts and process with each CSP/SaaS; test a tabletop exercise focused on account takeover or misconfiguration
Building Sustainable Cloud Security Governance: 90–180 Days
After stabilizing high-impact exposures, institutions should focus on sustainable governance and assurance:
- Document shared responsibility per service; map to NIST 800-53 controls and assign owners
- Harden configurations using authoritative baselines; enforce via policy-as-code and CI/CD checks
- Implement conditional access and device trust for risky actions; require just-in-time elevation and approval workflows for privileged tasks
- Strengthen third-party contracts with audit/access rights, log/forensic access, breach notification SLAs, sub-outsourcing transparency, and exit assistance
- Backups: maintain immutable, encrypted off-platform copies; test restoration and crypto-shredding on exit
- Measure and report on MFA coverage, privileged account reductions, high-risk configuration findings, log coverage, and incident response metrics
Maturing Cloud Security and Addressing Concentration Risk: 6–18 Months
Longer-term efforts should focus on maturing controls, testing resilience, and addressing concentration risk:
- Adopt Zero Trust Architecture patterns for high-value assets; extend micro-segmentation and continuous verification
- Integrate secure software development practices into pipelines; scan IaC and container images; manage secrets and SBOMs
- Conduct periodic red-teaming and threat-led testing focused on cloud control plane and identity
- Assess concentration risk, develop playbooks for degraded-mode operations and provider failure, and consider multi-region/multi-provider strategies where appropriate
- Automate evidence collection for control effectiveness and periodically attest to regulators and internal audit
Cloud Security Contract and Due Diligence Checklist for Financial Institutions
Institutions should ensure their contracts with cloud providers address the following areas:
- Access and audit rights, including risk-based onsite audit options and independent assurance reports
- Alignment to security baselines such as NIST 800-53 or FedRAMP High
- Guaranteed access to relevant logs and support for eDiscovery and incident forensics
- Incident management obligations, including notification windows and joint investigations
- Data protection standards, key ownership options, and data location commitments
- Operational resilience commitments, including RTO/RPO, change management transparency, and severe event communications
- Sub-outsourcing approval and notification, equivalent security obligations, and right to object where material
- Exit and portability provisions, including data export formats, transition assistance, and continued access to logs during transition
Close the Cloud Security Gap with NETBankAudit’s Financial Services Expertise
The cloud security gap in financial services is a multifaceted challenge that requires coordinated action across governance, identity, configuration, logging, resilience, and third-party management. NETBankAudit’s team of experts brings decades of experience in IT audit, cybersecurity, and regulatory compliance for financial institutions. Our tailored cloud security assessments, third-party risk reviews, and operational resilience testing help you align with FFIEC, NIST, CISA, and other regulatory expectations, while providing actionable recommendations to strengthen your security posture. Contact NETBankAudit today for a request for proposal and take the next step in closing your cloud security gap.
.avif)

.svg)

.webp)


.webp)




.webp)
.png)



.webp)

.webp)











.webp)



.webp)

%201.webp)
.webp)
%20(3).webp)


.webp)


%20Works.webp)


.webp)




.webp)
%20(1).webp)

.webp)










.webp)
.webp)

.webp)
.webp)
.webp)
.webp)
.webp)
.webp)
%201.svg)