The Cybersecurity and Infrastructure Security Agency (CISA) has released a forward-looking roadmap for the Common Vulnerabilities and Exposures (CVE) program, ushering in what it calls the “Quality Era.” This new phase is designed to elevate the trustworthiness, responsiveness, and quality of vulnerability data, with significant implications for regulated sectors such as financial services. For compliance professionals, understanding the roadmap’s priorities and aligning internal processes is now essential for both regulatory and operational resilience.
NETBankAudit experts have over 25 years of experience in vulnerability management audits and cybersecurity compliance for financial institutions. If you have any questions after reading this guide, please reach out to our team.
Understanding the CVE Program and the Quality Era Roadmap
The CVE Program: A Global Standard for Vulnerability Identification
Since its inception, the CVE Program has become the global benchmark for identifying and cataloging cybersecurity vulnerabilities. Over the past decade, the program has expanded to include more than 460 CVE Numbering Authorities (CNAs) worldwide, fueling exponential growth in the community’s ability to define and track vulnerabilities. This extensive network underpins vulnerability management, risk assessment, and regulatory compliance across industries, including financial services.

The “Quality Era”: A New Focus on Trust, Responsiveness, and Data Quality
CISA’s roadmap marks a strategic shift from the “Growth Era” to the “Quality Era.” The new focus is on ensuring that CVE data is not only comprehensive but also trustworthy, timely, and actionable. The initiative is built on several core principles:
- Maintaining CVE as a Public Good: CISA emphasizes that CVE data must remain free and openly accessible, supporting coordinated cyber defense and innovation in security tooling.
- Vendor-Neutral Stewardship: The program will be led with a commitment to conflict-free, transparent, and accountable leadership, avoiding the pitfalls of privatization that could compromise transparency and stability.
- Global and Multi-Sector Engagement: CISA is expanding partnerships to ensure representation from international organizations, academia, security researchers, operational technology, and the open-source community.
These priorities are designed to ensure that the CVE Program continues to serve as a trusted public good, supporting defenders across industry and government.
Key Pillars of the CVE Quality Era

Expanding Community Partnerships
CISA is committed to broadening the CVE Program’s advisory board to reflect the full diversity of the cybersecurity ecosystem. By engaging international organizations, governments, academia, vulnerability tool providers, and the open-source community, the program aims to foster valuable insights and drive innovation. This collaborative approach is expected to yield a more resilient and effective vulnerability management ecosystem.
Government Sponsorship and Sustainable Funding
As a critical public good, the CVE Program’s infrastructure requires ongoing investment. CISA is evaluating alternative funding sources to ensure the program’s long-term sustainability while maintaining its public and vendor-neutral character. Updates on funding mechanisms will be communicated to the community as they develop.
Modernization and Automation
To meet the demands of a global, operational program, CISA is accelerating the modernization of CVE infrastructure. This includes:
- Rapid implementation of automation to streamline CNA services
- Expanding API support for downstream data consumers
- Enhancing the CVE.org platform for improved accessibility and usability
These efforts are intended to make vulnerability data more accessible, timely, and actionable for all stakeholders.
Transparency and Communication
Transparency is central to building and maintaining trust in the CVE Program. CISA is committed to:
- Regularly communicating program milestones and performance metrics
- Actively seeking and incorporating community feedback into roadmap decisions
- Engaging in ongoing dialogue with global partners
This open approach ensures that the program remains responsive to the needs of its diverse user base.
Data Quality Improvements
CISA is tracking and improving the completeness and quality of CVE records. As of August 2025, nearly 80% of CNAs included critical scoring and classification information in their CVE publications, a significant improvement over the previous year. CISA is partnering with industry and international governments to implement new minimum standards for CVE record quality and to develop federated mechanisms for data enrichment, such as Vulnrichment and the Authorized Data Publisher (ADP) capability.=
Innovative solutions, including automation, machine learning, and artificial intelligence, are being explored to further enhance the quality and utility of CVE data.

Improvements in CNA of Last Resort (LR)
CISA is prioritizing transparency, visibility, and responsiveness in the CNA of Last Resort role. By raising standards for communication and data enrichment, CISA aims to set an example for the broader CNA community and ensure that all CVE records meet the highest standards of quality and reliability.
Implications for Financial Institutions: Risk, Compliance, and Strategic Planning
Regulatory Expectations and Industry Standards
Financial institutions operate in one of the most heavily regulated environments, with agencies such as the FFIEC, OCC, and SEC mandating robust vulnerability management and incident response programs. Compliance with standards like GLBA and NYDFS Cybersecurity Regulation often depends on the ability to demonstrate timely patching and effective vulnerability remediation.
Enhanced CVE data quality enables institutions to:
- Conduct more accurate and defensible risk assessments
- Prioritize remediation of vulnerabilities that pose the greatest risk to critical assets
- Document compliance efforts and demonstrate due diligence to regulators
Institutions that fail to align with these evolving standards risk regulatory scrutiny, reputational damage, and increased exposure to cyber threats.
Strategic Actions for Compliance Professionals
To stay ahead of regulatory expectations and emerging threats, compliance professionals should take a proactive approach. This includes:
- Reviewing and updating vulnerability management policies to reflect CISA’s new standards
- Ensuring integration of automated tools with CVE data feeds for real-time risk assessment
- Participating in sector-specific information sharing organizations such as FS-ISAC
- Monitoring CISA’s roadmap implementation and adjusting cybersecurity strategies accordingly
Public-Private Partnerships and Information Sharing: A Force Multiplier
The Value of Collaboration in Cybersecurity
CISA’s roadmap highlights the importance of public-private partnerships and information sharing in strengthening the cybersecurity ecosystem. Programs such as the Cyber Information Sharing and Collaboration Program (CISCP) and sector-specific ISACs (e.g., FS-ISAC) play a pivotal role in disseminating vulnerability and threat intelligence.
Organizations that actively participate in these networks benefit from:
- Faster detection and remediation of vulnerabilities
- Access to timely, actionable intelligence on emerging threats
- Opportunities to provide feedback and shape the evolution of the CVE program
Transparency in vulnerability reporting builds trust and enables informed risk management decisions. CISA’s roadmap encourages broader participation in the CVE program, including expanding the network of CNAs and improving feedback mechanisms.
Case Studies and Current Events: Lessons from Recent Incidents
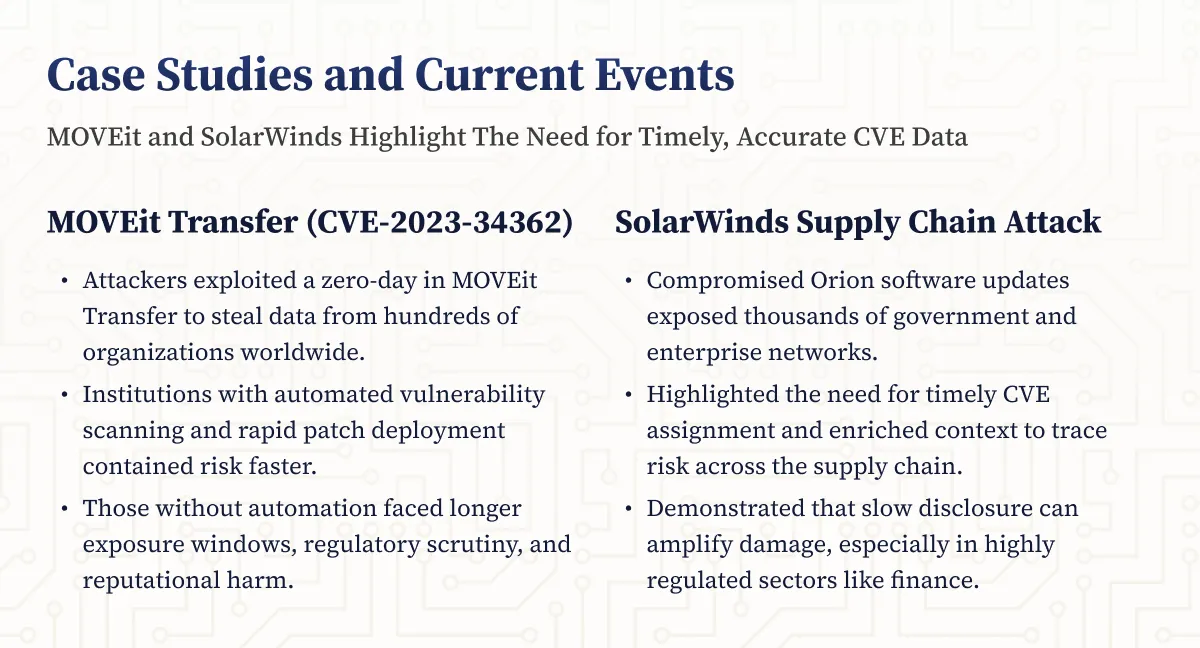
MOVEit, SolarWinds, and Log4j: The Need for Timely, Accurate CVE Data
Recent high-profile incidents such as the MOVEit Transfer vulnerability (CVE-2023-34362), SolarWinds, and Log4j have underscored the critical importance of rapid, accurate CVE reporting and industry-wide collaboration. Financial institutions affected by these events faced intense regulatory scrutiny and were required to demonstrate effective vulnerability management and incident response.
Key takeaways from these incidents include:
- Organizations with automated vulnerability management and strong information sharing practices responded more effectively to emerging threats
- Regulators are increasingly issuing guidance and enforcement actions related to timely patching and vulnerability disclosure
- Integrating CVE data with risk management and compliance frameworks reduces exposure and supports regulatory compliance
Recommended Actions for Financial Institutions
Proactive Steps for Alignment and Resilience
To align with CISA’s CVE roadmap and enhance cybersecurity posture, financial institutions should take the following proactive steps:
- Review and update vulnerability management policies to incorporate CISA’s new standards and best practices
- Integrate automated vulnerability scanning, risk scoring, and patch management tools with CVE data feeds
- Participate in sector-specific information sharing organizations (e.g., FS-ISAC) and CISA partnership programs
- Ensure compliance with regulatory requirements by documenting risk assessments, remediation actions, and incident response procedures
- Monitor CISA’s roadmap implementation and adjust cybersecurity strategies to address emerging threats and regulatory changes
These actions will position institutions to meet regulatory expectations, reduce cyber risk, and build operational resilience in an increasingly complex threat environment.
How NETBankAudit Can Help
NETBankAudit specializes in vulnerability management audits, cybersecurity risk assessments, and regulatory compliance services tailored for financial institutions. Our team leverages deep industry expertise and a proven methodology to help clients:
- Assess and enhance vulnerability management programs in line with CISA’s latest standards
- Integrate automated tools and CVE data feeds for real-time risk management
- Prepare for regulatory examinations and demonstrate compliance with FFIEC, GLBA, and NYDFS requirements
- Facilitate participation in information sharing networks and public-private partnerships
With over two decades of experience, NETBankAudit delivers actionable insights and practical solutions to strengthen your institution’s cybersecurity posture. Contact us today to discuss how we can support your compliance and risk management objectives in the evolving “Quality Era” of the CVE program.
%201%20(1).svg)
%201.svg)
.avif)

.svg)

.webp)


.webp)




.webp)
.png)



.webp)

.webp)











.webp)



.webp)

%201.webp)
.webp)
%20(3).webp)


.webp)


%20Works.webp)


.webp)




.webp)
%20(1).webp)

.webp)










.webp)
.webp)

.webp)
.webp)
.webp)
.webp)
.webp)
.webp)
%201.svg)