In 2025, financial institutions have become prime targets for cybercriminals exploiting critical software vulnerabilities. Attackers are leveraging flaws in web frameworks, remote access appliances, and core infrastructure to gain unauthorized access, steal data, and disrupt operations. For compliance professionals, understanding which vulnerabilities are most actively exploited, and how to address them, is essential for maintaining security and meeting regulatory expectations.
NETBankAudit experts have over 25 years of experience in vulnerability management, IT audits, and regulatory compliance for financial institutions. If you have any questions after reading this guide, please reach out to our team.
What Are CVEs and Where Can You Find Them?
Understanding CVEs: The Global Standard for Vulnerability Tracking
CVEs, or Common Vulnerabilities and Exposures, are unique identifiers assigned to publicly known cybersecurity vulnerabilities. Each CVE entry provides a standardized description, affected products, and technical details. The CVE system, managed by the MITRE Corporation, is the global standard for vulnerability identification and communication. Security professionals, vendors, and regulators use CVEs to track, prioritize, and remediate vulnerabilities across software and hardware ecosystems. This system enables organizations to speak a common language when discussing security flaws, making it easier to coordinate responses and share threat intelligence.
Where to Find Authoritative CVE Information
The most authoritative source for CVE details is the National Vulnerability Database (NVD). The NVD provides technical descriptions, severity scores (CVSS), and links to vendor advisories for each CVE. In addition to the NVD, organizations such as CISA, Microsoft, Cisco, and Citrix publish their own advisories and alerts, often providing additional context on exploitation status and mitigation strategies. Security researchers and industry blogs also offer timely updates on active threats, proof-of-concept exploits, and remediation best practices.
CVEs and Regulatory Compliance
Regulatory bodies expect financial institutions to demonstrate proactive vulnerability management. This includes tracking CVEs, assessing their relevance, and remediating critical flaws within defined timeframes. CISA’s Known Exploited Vulnerabilities (KEV) catalog, for example, highlights CVEs that are actively being exploited, and federal agencies are often required to patch these vulnerabilities within 24 to 48 hours of inclusion. Financial institutions are held to similar standards by industry regulators and must be able to show that they are keeping pace with the evolving threat landscape.
.webp)
What’s Next: The Top 5 CVEs for Financial Institutions in 2025
Cyber Security News compiled a list of the top 20 most exploited vulnerabilities of 2025. The following sections break down the five most relevant CVEs from that list for financial institutions. Each entry explains the vulnerability, its impact, and practical steps for mitigation. Compliance professionals should use this list to prioritize patching and strengthen their institution’s defenses against real-world threats.
%201%20(1).svg)
%201.svg)
THE GOLD STANDARD INCybersecurity and Regulatory Compliance
1. CVE-2025-55182: React2Shell – Unauthenticated Remote Code Execution in Meta React Server Components
_%20Unauthenticated%20RCE%20in%20Meta%20React%20Server%20Components.webp)
Critical Risk: Unauthenticated RCE in Cloud and Web Environments
React2Shell (CVE-2025-55182) is the most critical vulnerability of 2025, with a CVSS score of 10.0. It affects Meta React Server Components (RSC) and allows unauthenticated remote code execution via insecure deserialization of RSC Flight protocol payloads. Attackers can submit malicious serialized data, triggering arbitrary code execution on the server. This flaw has been widely exploited in cloud environments, with attackers deploying cryptocurrency miners and persistence agents using SYSTEM-level access. Financial institutions leveraging React-based web applications or cloud services are at significant risk, as exploitation can lead to full server compromise and lateral movement within internal networks. Multiple security teams, including Microsoft Defender and Google Threat Intelligence, have documented global exploit attempts, confirming the urgency for immediate remediation and patching of affected systems.
Why React2Shell Is a Top Concern for Financial Institutions
- Enables SYSTEM-level access on vulnerable servers, risking data theft and ransomware.
- Cloud environments are especially at risk due to rapid scanning and exploitation.
- Proof-of-concept code is public, and exploitation is widespread across threat actor groups.
Key Actions for Financial Institutions
- Patch all affected React Server Components immediately to eliminate the vulnerability.
- Audit web application exposure to the RSC protocol and review deserialization controls to prevent similar flaws.
- Monitor for suspicious serialized payloads targeting React infrastructure, using both automated tools and manual review.
- Review cloud workload configurations to ensure that unnecessary exposure is minimized and that access controls are properly enforced.
Real-World Exploitation and Industry Response
Shortly after disclosure, exploit attempts targeting cloud environments were observed worldwide. Attackers leveraged the vulnerability to gain SYSTEM-level access, deploy cryptocurrency miners, and establish persistence agents. The speed and scale of exploitation prompted urgent advisories from Microsoft Defender, Google Threat Intelligence, and Wiz Research. These advisories emphasized the need for immediate patching and highlighted the risk to organizations with exposed web applications or APIs. Financial institutions should treat React2Shell as a top priority for remediation and ensure that all relevant systems are updated without delay.
2. CVE-2025-32433: Erlang/OTP SSH Daemon Pre-Authentication Remote Code Execution
_%20Pre-Authentication%20Remote%20Code%20Execution.webp)
Pre-Authentication RCE: A Direct Path to System Compromise
CVE-2025-32433 is a critical pre-authentication remote code execution vulnerability in the SSH daemon implementation of Erlang/OTP, with a CVSS score of 10.0. The flaw arises from improper handling of SSH protocol messages before authentication is completed, allowing remote attackers to send crafted packets and execute arbitrary code without valid credentials. This vulnerability is particularly dangerous for financial institutions that rely on Erlang/OTP for backend services, messaging, or operational technology environments. Exploitation grants attackers full system compromise, including the ability to escalate privileges and move laterally within the network.
Key Implications for Compliance and Security Teams
- Bypasses traditional access controls, making it attractive to both opportunistic and targeted attackers.
- Active exploit attempts have been observed, especially in operational technology and telecom environments.
- Any exposed SSH service running vulnerable Erlang/OTP versions is at risk.
Mitigation Steps for Compliance Teams
- Patch to fixed versions (OTP-27.3.3, OTP-26.2.5.11, OTP-25.3.2.20 or later) as soon as possible.
- Restrict SSH access via firewall rules until patching is complete, limiting exposure to trusted networks only.
- Consider disabling the SSH server entirely if operationally feasible, especially on systems that do not require remote access.
- Include rapid isolation and forensic analysis in incident response plans for systems running Erlang/OTP SSH daemons.
Threat Intelligence and Regulatory Context
The vulnerability was quickly added to the CISA Known Exploited Vulnerabilities catalog, signaling active exploitation and significant risk. Security advisories from Unit42 and Arctic Wolf provided technical details on the exploitation mechanism and recommended immediate patching. Financial institutions should ensure that all exposed SSH services are inventoried, patched, and monitored for signs of exploitation. Incident response teams should be prepared to isolate affected systems and conduct forensic analysis to determine the extent of any compromise.
3. CVE-2025-20333: Cisco ASA/FTD Authenticated Remote Code Execution
_%20Firewall%20Exploitation%20Chain.webp)
Firewall Exploitation Chain: Perimeter Devices Under Siege
CVE-2025-20333 is a buffer overflow vulnerability in the VPN web server component of Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) devices. With a CVSS score of 9.9, this flaw allows authenticated attackers to execute arbitrary code as root. It is often exploited in conjunction with CVE-2025-20362, which enables unauthenticated access to restricted URL endpoints. Together, these vulnerabilities form an exploitation chain that has been actively used in state-sponsored espionage campaigns, including those attributed to the ArcaneDoor threat actor. Financial institutions relying on Cisco ASA/FTD for perimeter defense are at heightened risk, as successful exploitation can lead to full device compromise, malware deployment, and denial-of-service conditions.
Immediate Actions for Financial Institutions
- Patch all affected Cisco ASA and FTD devices to the latest supported versions.
- Review VPN access logs and firewall rules for suspicious activity or exploitation attempts.
- Implement network segmentation and multi-factor authentication to limit the impact of device compromise.
- Monitor for unexpected device reboots, which may indicate exploitation attempts or successful attacks.
4. CVE-2025-59287: Microsoft WSUS Deserialization Remote Code Execution
_%20Deserialization%20Remote%20Code%20Execution.webp)
Patch Management Infrastructure at Risk
CVE-2025-59287 is a critical remote code execution vulnerability in Microsoft Windows Server Update Services (WSUS), with a CVSS score of 9.8. The flaw results from unsafe deserialization of crafted requests, allowing attackers to achieve SYSTEM privileges and execute reconnaissance or lateral movement commands within the network. This vulnerability is especially concerning for financial institutions, as WSUS is a central component of patch management infrastructure. Exploitation was confirmed within hours of Microsoft’s emergency patch release, prompting immediate inclusion in the CISA Known Exploited Vulnerabilities catalog. Attackers have leveraged this flaw to compromise internal networks, highlighting the importance of timely patching and strict access controls on WSUS servers.
Key Mitigation Priorities
- Apply Microsoft’s out-of-band security update immediately to all WSUS servers.
- Restrict network access to WSUS servers, limiting exposure to trusted systems only.
- Monitor for suspicious deserialization activity and anomalous behavior on WSUS servers.
- Review patch management workflows and access controls to ensure compliance with regulatory expectations.
5. CVE-2025-5777: CitrixBleed 2 – Citrix NetScaler ADC/Gateway Memory Disclosure
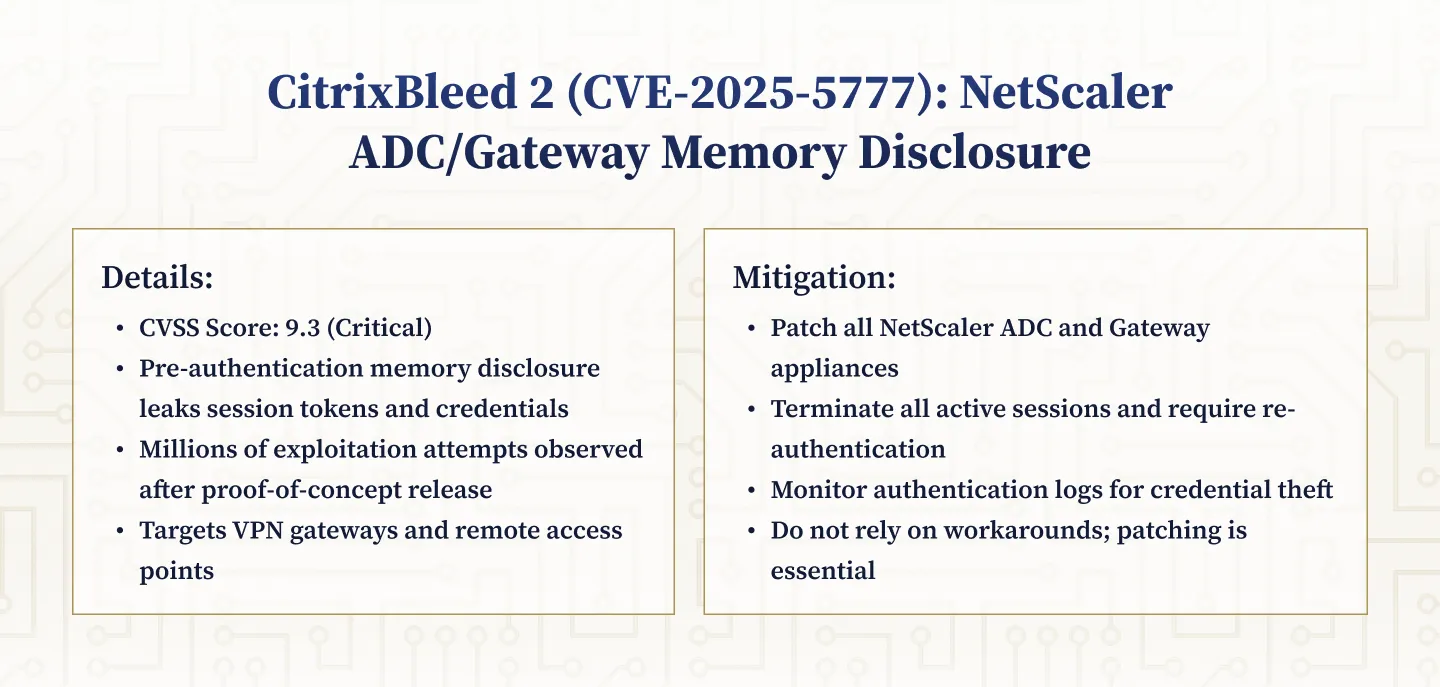
Memory Disclosure: Credential and Session Token Exposure
CVE-2025-5777, dubbed “CitrixBleed 2,” is a pre-authentication memory disclosure vulnerability affecting Citrix NetScaler ADC and Gateway appliances. With a CVSS score of 9.3, this flaw allows unauthenticated attackers to leak sensitive memory contents, including session tokens and credentials, by exploiting improper input validation in HTTP POST authentication requests. NetScaler devices are widely used as VPN gateways and remote access points in financial institutions, making this vulnerability a prime target for attackers. CISA added CVE-2025-5777 to the Known Exploited Vulnerabilities catalog, and security researchers reported millions of exploitation attempts shortly after proof-of-concept code was released. The risk is amplified by the potential for attackers to harvest authentication material and gain unauthorized access to internal systems.
Urgent Remediation Steps
- Patch all vulnerable NetScaler ADC and Gateway appliances to supported versions that include the fix.
- Terminate all active sessions and require re-authentication for remote users to prevent session hijacking.
- Monitor for anomalous access patterns and review authentication logs for evidence of credential theft or unauthorized access.
- Do not rely on workaround steps, as memory disclosure cannot be fully mitigated without patching.
Threat Activity and Exposure
Security researchers observed millions of exploitation attempts targeting financial services environments shortly after proof-of-concept code was released. Attackers are using this vulnerability to harvest session tokens, credentials, and other sensitive data, which can then be used to gain unauthorized access to internal systems. The widespread use of NetScaler devices as VPN gateways makes this vulnerability particularly dangerous for financial institutions. Immediate patching and session termination are essential to prevent unauthorized access and limit the impact of exploitation.
Industry Context and Regulatory Implications
Escalating Threats and Compliance Expectations
The escalation in exploitation of these five vulnerabilities highlights the evolving threat landscape facing financial institutions. Attackers are increasingly targeting core infrastructure components, remote access systems, and patch management platforms, often chaining vulnerabilities to maximize impact. Regulatory bodies such as CISA and the U.K. NCSC have issued emergency directives and advisories, emphasizing the need for rapid identification, patching, and monitoring of affected systems. Compliance professionals must ensure that vulnerability management programs are robust, up-to-date, and capable of responding to emerging threats in real time. Failure to address these vulnerabilities can result in regulatory penalties, reputational damage, and significant financial losses.
How NETBankAudit Can Help
Staying ahead of rapidly evolving threats requires more than just patching. NETBankAudit offers specialized vulnerability assessment, penetration testing, and IT audit services tailored to the unique needs of financial institutions. Our team leverages deep industry expertise and up-to-date threat intelligence to help you identify, prioritize, and remediate critical vulnerabilities before they can be exploited. To strengthen your institution’s security posture and ensure regulatory compliance, contact NETBankAudit today.
.avif)

.svg)



.webp)




.webp)
.png)




.webp)

.webp)











.webp)



.webp)

%201.webp)
.webp)
%20(3).webp)


.webp)


%20Works.webp)


.webp)




.webp)
%20(1).webp)

.webp)










.webp)
.webp)

.webp)
.webp)
.webp)
.webp)
.webp)
.webp)
%201.svg)