Ransomware remains one of the most significant cyber threats facing the financial sector, with the potential to disrupt operations, compromise sensitive data, and inflict substantial financial losses. Between 2022 and 2024, Bank Secrecy Act (BSA) data and regulatory reports reveal evolving attack patterns, payment trends, and supervisory expectations that compliance professionals must understand to strengthen their institution’s resilience and response capabilities.
NETBankAudit experts have decades of experience in BSA/AML, cybersecurity, and operational resilience audits for financial institutions. If you have questions about ransomware trends or compliance strategies after reading this guide, please contact our team.
Ransomware Incidents and Payments: BSA Data Trends

2023 Marked an All-Time High in Ransomware Activity and Payments
According to the Financial Crimes Enforcement Network (FinCEN), ransomware incidents and payments reported in BSA filings reached unprecedented levels in 2023. That year, financial institutions filed 1,512 BSA reports tied to ransomware, with reported payments totaling approximately $1.1 billion, a 77 percent increase in aggregate payment value compared to 2022. In 2024, the number of incidents declined slightly to 1,476, and reported payments dropped to about $734 million, which still represented the third-highest annual total since BSA ransomware reporting began in 2013. These figures underscore the persistent and evolving threat ransomware poses to the financial sector and the broader economy.
Incident and Payment Volatility: What the Numbers Reveal
While the number of ransomware incidents fluctuated only modestly year over year, payment totals showed greater volatility. For example, incidents decreased by 14 percent from 2021 to 2022, then rose by 25 percent in 2023, before a slight 2 percent decrease in 2024. Payment values, however, surged and then fell sharply, reflecting changes in attack severity, negotiation outcomes, and the impact of law enforcement actions against major ransomware groups such as ALPHV/BlackCat and LockBit. These enforcement actions contributed to the notable drop in payments in 2024, even as incident counts remained high.

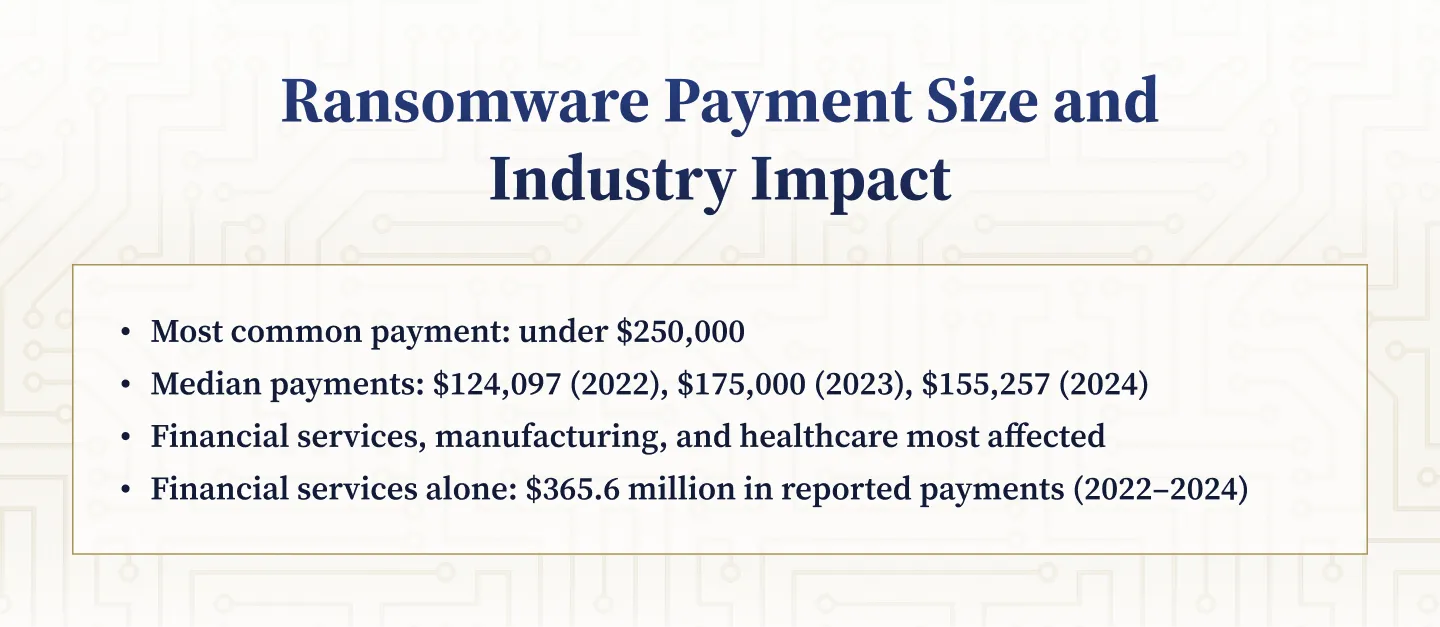
Payment Size Distribution and Industry Impact
The most common ransomware payment reported between 2022 and 2024 was below $250,000. Median payment values were $124,097 in 2022, $175,000 in 2023, and $155,257 in 2024. Despite the prevalence of smaller payments, aggregate losses reached billions due to the high volume of incidents and a tail of larger events. Financial services, manufacturing, and healthcare were the most affected industries, both in terms of incident frequency and total ransom paid. Financial services alone accounted for approximately $365.6 million in reported payments during the review period, highlighting the sector’s attractiveness to threat actors.
Ransomware Attack Patterns: Operational and Technical Insights
Modern Ransomware: Multi-Phase Extortion and Escalation
Ransomware attacks have evolved into sophisticated, multi-phase operations. The initial phase involves gaining access to the victim’s systems, deploying malware, encrypting files, and often exfiltrating sensitive data. Attackers frequently disable security and backup systems to maximize leverage. The second phase centers on extortion, with threat actors issuing ransom demands and employing pressure tactics such as threats to leak data (so-called “Leakware” or “Doxware”). Some groups escalate further, launching distributed denial of service (DDoS) attacks or contacting customers, employees, and regulators to accelerate payment—a tactic known as triple or quadruple extortion.
These operational realities mean that even if a financial institution refuses to pay, it may still face severe harm from data exposure, business disruption, and reputational damage. The time between detection and impact is often minimal, requiring institutions to execute crisis management plans in real time, sometimes without access to core tools or communications systems.
Common Intrusion Vectors and Enablement Models
Threat actors exploit a range of entry points to initiate ransomware attacks, including:
- Social engineering and phishing emails targeting employees
- Compromised credentials and weak authentication
- Zero-day exploits and unpatched software vulnerabilities
- Open network shares and remote access services
- Public-facing application and supply chain vulnerabilities
- Untargeted “drive-by downloads”
Human-operated ransomware, often facilitated by criminal ecosystems that sell initial access or offer “Ransomware-as-a-Service,” remains the dominant threat type. Attackers move laterally within networks, disable security tools, and exploit misconfigurations—trends that are increasingly enabled by advances in generative AI, which make it easier to identify and exploit weaknesses.
Ransomware Variants, Communication Channels, and Payment Methods

Variant Diversity and Concentration of Losses
FinCEN identified 267 unique ransomware variants in BSA data from 2022 to 2024. However, losses were heavily concentrated among a small set of variants. ALPHV/BlackCat and LockBit were the most impactful, with ALPHV/BlackCat alone accounting for approximately $395.3 million in reported payments. Akira, Phobos, and Black Basta were also among the most frequently reported variants. The top 10 variants collectively accounted for about $1.5 billion in suspicious activity, underscoring the importance of tracking and defending against these specific threats.
Communication and Negotiation Channels
Ransomware actors most commonly communicated with victims via The Onion Router (TOR) protocol, which was cited in 67 percent of BSA reports that specified a method. Email was the next most common channel, used in 28 percent of such reports. Negotiations typically occurred on attacker-provided “.onion” sites, with some threat actors escalating demands even after initial payments were made. These communication patterns highlight the need for institutions to monitor for suspicious network activity and to be prepared for complex, multi-stage negotiations.
Dominance of Bitcoin and Other Payment Rails
Bitcoin (BTC) was the overwhelmingly dominant payment method, accounting for 97 percent of reported ransomware transactions and approximately $2.0 billion in value. Monero (XMR) appeared in about 2 percent of reports, with Ether, Litecoin, and Tether on Ethereum used rarely. Threat actors typically collected payments in unhosted wallets and laundered proceeds through cryptocurrency exchanges, complicating efforts to trace and recover funds.
%201%20(1).svg)
%201.svg)
THE GOLD STANDARD INCybersecurity and Regulatory Compliance
Regulatory and Supervisory Expectations: OCC and BSA/AML Implications
Ransomware as a Safety and Soundness Issue
The Office of the Comptroller of the Currency (OCC) treats ransomware and related cyber threats as top supervisory priorities. Operational resilience and cybersecurity are central to the OCC’s Bank Supervision Operating Plan, and banks are expected to maintain robust internal controls, information security programs, and risk governance frameworks. The OCC’s safety and soundness standards (12 CFR 30, Appendix A and D) require effective risk assessment, asset safeguarding, and internal audit systems tailored to the institution’s size and risk profile.
Mandatory Reporting and Notification Requirements
OCC regulations require banks to file Suspicious Activity Reports (SARs) when they detect known or suspected violations of federal law, including ransomware incidents. In addition, the Computer-Security Incident Notification Rule (12 CFR 53) mandates that banks notify their primary federal regulator within 36 hours of determining that a significant incident has occurred. This notification regime operates in parallel with BSA/SAR reporting and is reinforced by emerging requirements under the Cyber Incident Reporting for Critical Infrastructure Act (CIRCIA), which will require certain incidents and ransomware payments to be reported to the Cybersecurity and Infrastructure Security Agency (CISA).
Third-Party and Supply Chain Risk Management
Ransomware risk is not limited to direct attacks on banks. The OCC emphasizes the importance of managing third-party and supply chain risks, as service providers can serve as entry points for ransomware propagation. Examinations of critical service providers are conducted jointly with other regulators and focus on core banking, payments, technology infrastructure, and other high-risk services. Banks are expected to assess and monitor third-party relationships, ensure contractual protections, and align technology architecture planning with cybersecurity programs to maintain operational resilience.
Defensive Controls and Crisis Management: Practical Steps for Financial Institutions
Technical and Organizational Controls to Reduce Ransomware Risk
While regulatory guidance emphasizes detection, reporting, and coordination with law enforcement, operational resilience depends on implementing a robust control stack. The following measures, drawn from FS-ISAC’s Cyber Fundamentals and industry best practices, are especially relevant for ransomware defense:
- Isolate, test, and exercise backups using non-erasable and non-modifiable systems; test restoration at least annually
- Regularly update and patch software, with automated patch management where feasible; use virtual patching (e.g., web application firewalls) if patching is delayed
- Adopt a zero-trust and least privilege policy, require multi-factor authentication, and enforce strong passwords for all users and devices
- Conduct regular employee training on phishing, social engineering, and safe computing practices
- Develop and exercise a ransomware-specific incident response plan, including tabletop and full-scale drills
- Implement endpoint detection and response (EDR), data loss prevention (DLP), and firewall solutions with internal segmentation and active blocking
These controls not only reduce the likelihood of a successful attack but also limit the pressure to pay ransoms by ensuring that critical data and systems can be restored quickly and securely.
Crisis Management and Communication Planning
Effective ransomware response requires a crisis management plan that accounts for the loss of access to key tools and systems. Plans should include:
- Clear policies on ransom payment, including legal review and pre-identified negotiation and cryptocurrency procurement processes
- Triggers and procedures for notifying insurance providers, regulators, law enforcement, and external experts
- Sequenced communication protocols for board, regulatory, employee, and public notifications
- Vendor impact assessment and third-party communication plans
- Forensic evidence preservation and chain of custody procedures
- Regular scenario-based exercises to validate and improve response capabilities
Institutions should ensure that crisis management teams include senior leadership, legal and risk management, public relations, operations, information security, vendor management, and human resources. This multidisciplinary approach is essential for coordinated, effective response during a high-impact ransomware event.
Sanctions, Payment Decisions, and Compliance Risks
Should You Pay? Legal and Regulatory Considerations
Both FinCEN and FS-ISAC strongly discourage paying ransoms, as doing so funds further criminal activity and may not guarantee data recovery. Payment risks include the possibility of not receiving decryption keys, facing follow-on demands, or being targeted again. Critically, paying a ransom may expose an institution to sanctions violations, especially if the recipient is a Specially Designated National (SDN) or otherwise subject to U.S. or international sanctions. Financial institutions must contact the Office of Foreign Assets Control (OFAC) if there is any reason to suspect a sanctions nexus and should ensure that any payment decision is supported by legal review and documented governance processes.
Institutions operating internationally should be aware of additional regulatory regimes, such as the UK’s cyber sanctions and Australia’s sanctions laws, which may impose further restrictions or penalties related to ransomware payments.
Emerging Threats and the Path Forward
Beyond Ransomware: Broader Cyber and Operational Risks
While ransomware remains a dominant threat, financial institutions must also contend with related risks such as account takeover, business email compromise, supply chain attacks, and the use of artificial intelligence to amplify phishing and malware campaigns. The OCC and other regulators highlight the importance of monitoring these threats, maintaining up-to-date technology infrastructure, and participating in sector-wide information sharing and resilience initiatives.
Public-private coordination is critical. Institutions are encouraged to engage with organizations such as the Financial Services Information Sharing and Analysis Center (FS-ISAC) and to monitor alerts from CISA and other government agencies. Regulatory expectations continue to evolve, with increasing emphasis on harmonized incident reporting, third-party risk management, and alignment with frameworks such as the NIST Cybersecurity Framework and FFIEC IT Examination Handbook.
Strengthening Your Institution’s Ransomware Resilience
Ransomware trends from 2022 to 2024 demonstrate that financial institutions remain prime targets for sophisticated, high-impact attacks. Compliance professionals must ensure that their organizations not only meet regulatory reporting and notification requirements but also implement robust technical, operational, and governance controls to prevent, detect, and respond to ransomware incidents.
NETBankAudit provides specialized audit and advisory services to help financial institutions assess and strengthen their ransomware defenses, incident response plans, and compliance programs. To discuss how we can support your institution’s resilience and regulatory readiness, please contact NETBankAudit today.
.avif)

.svg)

.webp)


.webp)




.webp)
.png)




.webp)

.webp)











.webp)



.webp)

%201.webp)
.webp)
%20(3).webp)


.webp)


%20Works.webp)


.webp)




.webp)
%20(1).webp)

.webp)










.webp)
.webp)

.webp)
.webp)
.webp)
.webp)
.webp)
.webp)
%201.svg)