With the sunsetting of FFIEC CAT/ACET, there are new cybersecurity frameworks to safeguard sensitive data, ensure regulatory compliance, and maintain operational resilience. The NIST Cybersecurity Framework (CSF) 2.0, CISA Cybersecurity Performance Goals (CPGs), and the Cyber Risk Institute (CRI) Profile 2.0 each offer unique strengths for building and enhancing cybersecurity programs. This guide provides an overview of these leading frameworks, highlighting their structure, areas of focus.

NETBankAudit experts have over 25 years of experience in cybersecurity audits and compliance. If you have any questions after reading this guide, please reach out to our team.
NIST Cybersecurity Framework 2.0 Overview
The NIST Cybersecurity Framework 2.0 can help an organization begin or improve their cybersecurity program. Built off of practices that are known to be effective, it can help organizations improve their cybersecurity posture. It fosters communication among both internal and external stakeholders about cybersecurity, and for larger organizations, helps to better integrate and align cybersecurity risk management with broader enterprise risk management processes.
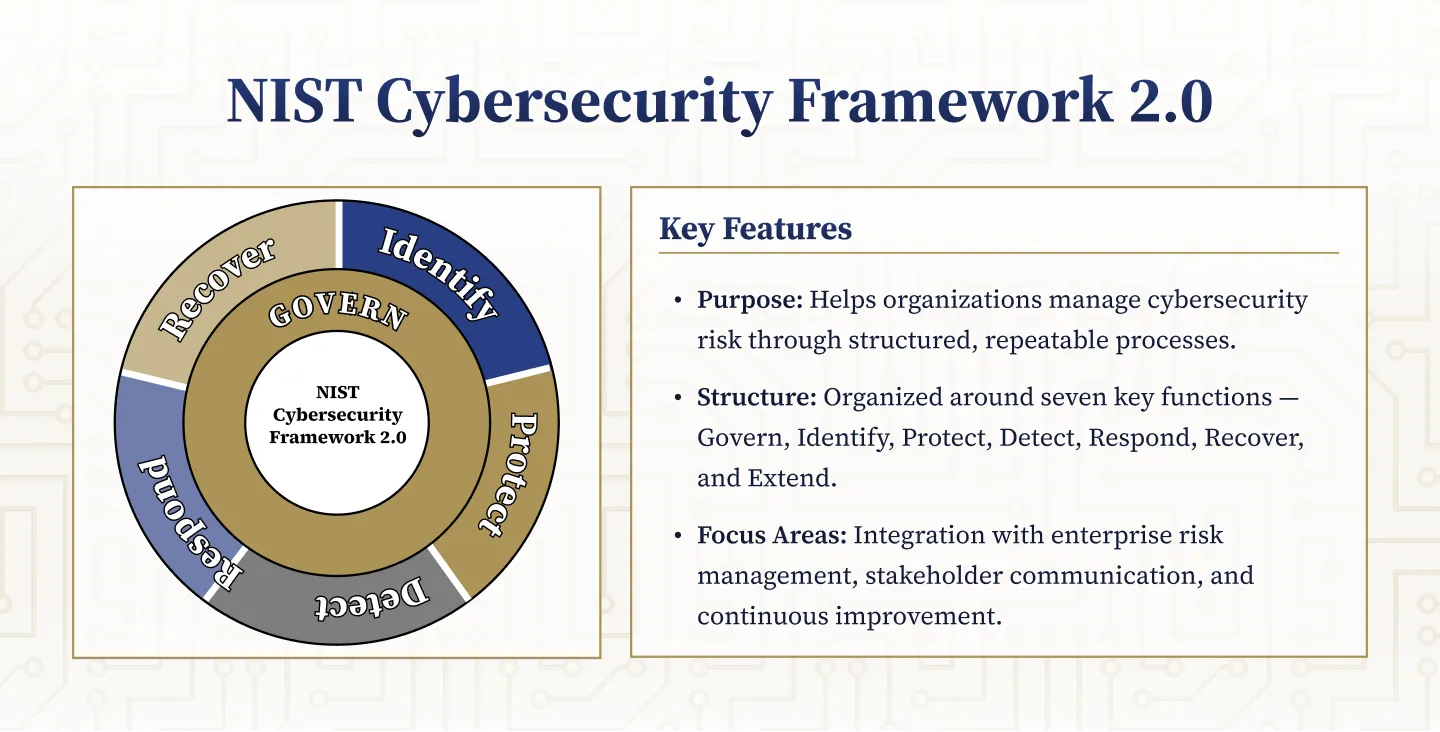
The Framework is organized by seven key Functions – Identify, Protect, Detect, Respond, and Recover. These seven widely understood terms, when considered together, provide a comprehensive view of the lifecycle for managing cybersecurity risk over time.
The Functions include categories, subcategories, and individual declarative statements across the five functions to identify specific controls and practices that are in place.
NIST CSF 2.0 Function Levels
An institution can use the NIST Framework as a key part of its systematic process for identifying, assessing, and managing cybersecurity risk.
NIST Cyber Security Framework (CSF) 2.0
The NIST Cyber Security Framework 2.0 defines needed controls within the following seven categories:
- Govern
- Organizational Context
- Risk Management Strategy
- Roles, Responsibilities, and Authorities
- Policies, Processes, and Procedures
- Oversight
- Supply Chain Management
- Independent Risk Management Function
- Independent Audit Function
- Identify
- Asset Management
- Risk Assessment
- Improvement
- Protect
- Identity Management, Authentication and Access Control
- Awareness and Training
- Data Security
- Platform Security
- Technology Infrastructure Resilience
- Detect
- Continuous Monitoring
- Adverse Event Analysis
- Respond
- Incident Management
- Incident Analysis
- Incident Response Reporting and Communication
- Incident Mitigation
- Recover
- Incident Recovery Plan Execution
- Incident Recovery Communication
- Extend
- Procurement Planning and Due Diligence
- Third-Party Contracts and Agreements
- Monitoring and Managing Suppliers
- Relationship Termination
The Framework is not designed to replace existing processes; an organization can use its current process and overlay it onto the Framework to determine gaps in its current cybersecurity risk approach and develop a roadmap to improvement. Using the Framework as a cybersecurity risk management tool, an organization can determine activities that are most important to critical service delivery and prioritize expenditures to maximize the impact of the investment.
Organizations can examine the extent to which they are achieving the outcomes described in the Core Categories and Subcategories, aligned with the seven high-level Functions: Govern, Identify, Protect, Detect, Respond, Recover, and Extend.
An organization may find that it is already achieving the desired outcomes, thus managing cybersecurity commensurate with the known risk. Alternatively, an organization may determine that it has opportunities to (or needs to) improve. The organization can use that information to develop an action plan to strengthen existing cybersecurity practices and reduce cybersecurity risk. An organization may also find that it is overinvesting to achieve certain outcomes. The organization can use this information to reprioritize resources.
CISA Cybersecurity Performance Goals Overview
The Cybersecurity and Infrastructure Security Agency’s (CISA) Cybersecurity Performance Goals (CPGs) can help an organization begin or improve their cybersecurity program. Built off of practices that are known to be effective (such as the NIST CSF 2.0 framework), it can help organizations improve their cybersecurity posture. It fosters communication among both internal and external stakeholders about cybersecurity, and for larger organizations, helps to better integrate and align cybersecurity risk management with broader enterprise risk management processes.
The CPGs are organized by five key functions: Identify, Protect, Detect, Respond, and Recover. These five widely understood terms, when considered together, provide a comprehensive view of the lifecycle for managing cybersecurity risk over time.
The Functions include categories, subcategories, and individual declarative statements across the five functions to identify specific controls and practices that are in place.
CISA CPG Function Levels
The CISA CPGs are an extension of the NIST CSF. The CISA CPGs extends the NIST CSF's scope by targeting more specific coverage of enterprise technology/OT (operational technology), network security, third-party risk management, incident response, and business continuity/resilience.
CISA CPGs
The CISA CPGs define needed controls within the following five categories:
- Identify
- Asset Inventory
- Organizational Cybersecurity Leadership
- Operational Technology (OT) Cybersecurity Leadership
- Improving IT and OT Cybersecurity Relationships
- Migrating Known Vulnerabilities
- Third Party Validation of Cybersecurity Control Effectiveness
- Supply Chain Incident Reporting
- Supply Chain Vulnerability Disclosure
- Vendor/Supplier Cybersecurity Requirements
- Protect
- Changing Default Passwords
- Minimum Password Strength
- Unique Credentials
- Revoking Credentials for Departing Employees
- Separating User and Privileged Accounts
- Network Segmentation
- Detection of Unsuccessful (Automated) Logon Attempts
- Phishing-Resistant Multifactor Authentication (MFA)
- Basic Cybersecurity Training
- OT Cybersecurity Training
- Strong and Agile Encryption
- Secure Sensitive Data
- Email Security
- Disable Macros by Default
- Document Device Configurations
- Document Network Topology
- Hardware and Software Approval Process
- System Backups
- Incident Response (IR) Plans
- Log Collection
- Secure Log Storage
- Prohibit Connection of Unauthorized Devices
- No Exploitable Services on the Internet
- Limit OT Connections to Public Internet
- Detect
- Detecting Relevant Threats and TTPs
- Respond
- Incident Reporting
- Vulnerability Disclosure/Reporting
- Recover
- Incident Planning and Preparedness
The CISA CPGs are not designed to replace existing processes; an organization can use its current process and overlay it onto the CPGs to determine gaps in its current cybersecurity risk approach and develop a roadmap to improvement. Using the CISA CPGs as a cybersecurity risk management tool, an organization can determine activities that are most important to critical service delivery and prioritize expenditures to maximize the impact of the investment.
Organizations can examine the extent to which they are achieving the outcomes described in the CPGs Recommended Actions, aligned with the five high-level functions: Identify, Protect, Detect, Respond, Recover.
An organization may find that it is already achieving the desired outcomes, thus managing cybersecurity commensurate with the known risk. Alternatively, an organization may determine that it has opportunities to (or needs to) improve. The organization can use that information to develop an action plan to strengthen existing cybersecurity practices and reduce cybersecurity risk. An organization may also find that it is overinvesting to achieve certain outcomes. The organization can use this information to reprioritize resources.
Cyber Risk Institute Profile 2.0 Overview
The Cyber Risk Institute Profile 2.0 can help an organization begin or improve their cybersecurity program. Built off of practices that are known to be effective (such as the NIST CSF 2.0 framework), it can help organizations improve their cybersecurity posture. It fosters communication among both internal and external stakeholders about cybersecurity, and for larger organizations, helps to better integrate and align cybersecurity risk management with broader enterprise risk management processes.
The Profile is organized by seven key functions: Govern, Identify, Protect, Detect, Respond, Recover, and Extend. These seven widely understood terms, when considered together, provide a comprehensive view of the lifecycle for managing cybersecurity risk over time.
The Functions include categories, subcategories, and individual declarative statements across the five functions to identify specific controls and practices that are in place.
CRI Function Levels
The CRI Profile is an extension of the NIST CSF developed by and for the financial services sector. The CRI Profile extends the NIST CSF's scope by targeting more specific coverage of enterprise technology/ICT, third-party risk management, and business continuity/resilience.
Cyber Risk Institute (CRI) Profile 2.0
The CRI Profile 2.0 defines needed controls within the following seven categories:
- Govern
- Organizational Context
- Risk Management Strategy
- Roles, Responsibilities, and Authorities
- Policies, Processes, and Procedures
- Oversight
- Supply Chain Management
- Independent Risk Management Function
- Independent Audit Function
- Identify
- Asset Management
- Risk Assessment
- Improvement
- Protect
- Identity Management, Authentication and Access Control
- Awareness and Training
- Data Security
- Platform Security
- Technology Infrastructure Resilience
- Detect
- Continuous Monitoring
- Adverse Event Analysis
- Respond
- Incident Management
- Incident Analysis
- Incident Response Reporting and Communication
- Incident Mitigation
- Recover
- Incident Recovery Plan Execution
- Incident Recovery Communication
- Extend
- Procurement Planning and Due Diligence
- Third-Party Contracts and Agreements
- Monitoring and Managing Suppliers
- Relationship Termination
The CRI Profile is not designed to replace existing processes; an organization can use its current process and overlay it onto the Profile to determine gaps in its current cybersecurity risk approach and develop a roadmap to improvement. Using the CRI Profile as a cybersecurity risk management tool, an organization can determine activities that are most important to critical service delivery and prioritize expenditures to maximize the impact of the investment.
Organizations can examine the extent to which they are achieving the outcomes described in the Core Categories and Subcategories, aligned with the seven high-level Functions: Govern, Identify, Protect, Detect, Respond, Recover, and Extend.
An organization may find that it is already achieving the desired outcomes, thus managing cybersecurity commensurate with the known risk. Alternatively, an organization may determine that it has opportunities to (or needs to) improve. The organization can use that information to develop an action plan to strengthen existing cybersecurity practices and reduce cybersecurity risk. An organization may also find that it is overinvesting to achieve certain outcomes. The organization can use this information to reprioritize resources.
NETBankAudit’s Cybersecurity and Information Security Program Review
NETBankAudit offers a specialized review of cybersecurity and information security programs, benchmarking them against FFIEC guidelines and leading industry standards such as NIST, CISA, and CRI. This Information Security review evaluates the effectiveness of documented programs and compliance with regulatory requirements, including the GLB Act 501(b).
The cybersecurity program will evaluate current practices and overall cybersecurity preparedness to determine effectiveness and inclusion of appropriate risk management and oversight, threat intelligence and collaboration, cybersecurity controls, external dependency management, and cyber incident management and resilience.
NETBankAudit will also review the client’s GLBA Information Security Risk Assessment and the Cybersecurity Assessment Tool (FFIEC, NIST, CISA, CRI, etc.) for input into the audits of relevant control areas. Specialized cybersecurity testing may also be incorporated into the internal and external network vulnerability assessment to validate controls.
Why Choose NETBankAudit?
With over 25 years of experience, NETBankAudit delivers unmatched expertise in cybersecurity audits and compliance for financial institutions. Our team provides tailored recommendations, actionable insights, and ongoing support to help your institution achieve and maintain a strong cybersecurity posture. We understand the unique challenges faced by financial institutions and are committed to helping you navigate the complexities of regulatory compliance and risk management.
%201%20(1).svg)
%201.svg)
.avif)

.svg)

.webp)


.webp)



.webp)
.png)




.webp)

.webp)











.webp)



.webp)

%201.webp)
.webp)
%20(3).webp)


.webp)


%20Works.webp)


.webp)




.webp)
%20(1).webp)

.webp)










.webp)
.webp)

.webp)
.webp)
.webp)
.webp)
.webp)
.webp)
%201.svg)